VPNs and Tor
Dr. Greg Bernstein
August 4th, 2021
VPNs
References: VPNs
- Everything VPN Is New Again By David Crawshaw, Communications of the ACM, April 2021, Vol. 64 No. 4, Pages 130-134. Main reading
- WireGuard, the new simpler, better, approach to secure tunnels.
- 100% Anonymous VPN: Does it really exist?
- Defend Dissent
VPN History Overview
- Private networks built with “leased lines”
- Tunneling across the internet, as a “cheaper leased line”
- Securing everything with IPSec anyway you want to if you can figure it out
- Satellite offices, road warriors, remote workers via OpenVPN protocol uses SSL/TLS
- Anonymity for consumers and others…
- Single user devices, zero trust, move towards simplicity Wireguard
Building Networks
- Networks are built out of communication links and switches (also referred to as nodes)
- Links operate at a particular layer, e.g., IP, Ethernet, MPLS, SDH, G.709, WDM, etc…
- Switches operate at at least one layer. Switches may also be called routers, ADM, etc depending on layer
Example Abstract Network
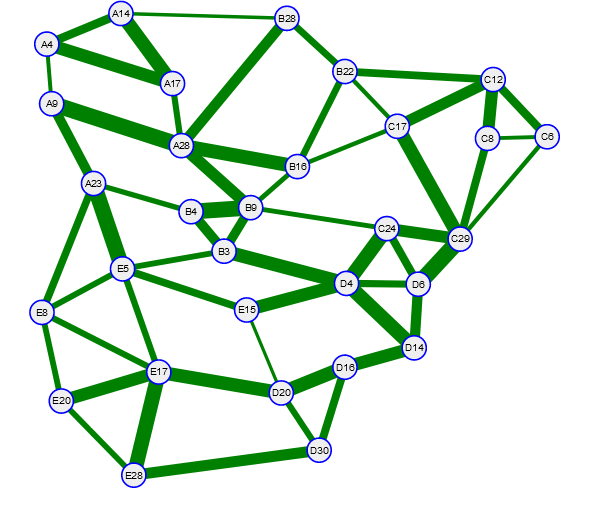
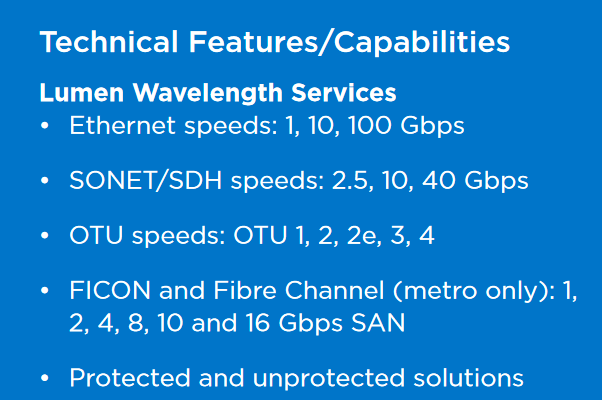
Wavelength Service Example 1
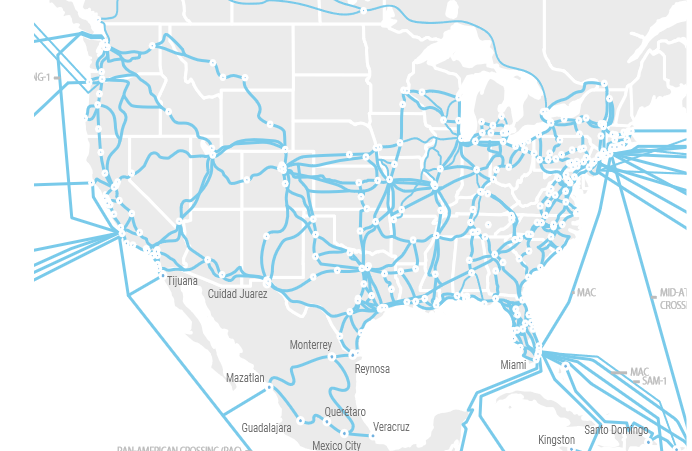
Wavelength Service Example 2
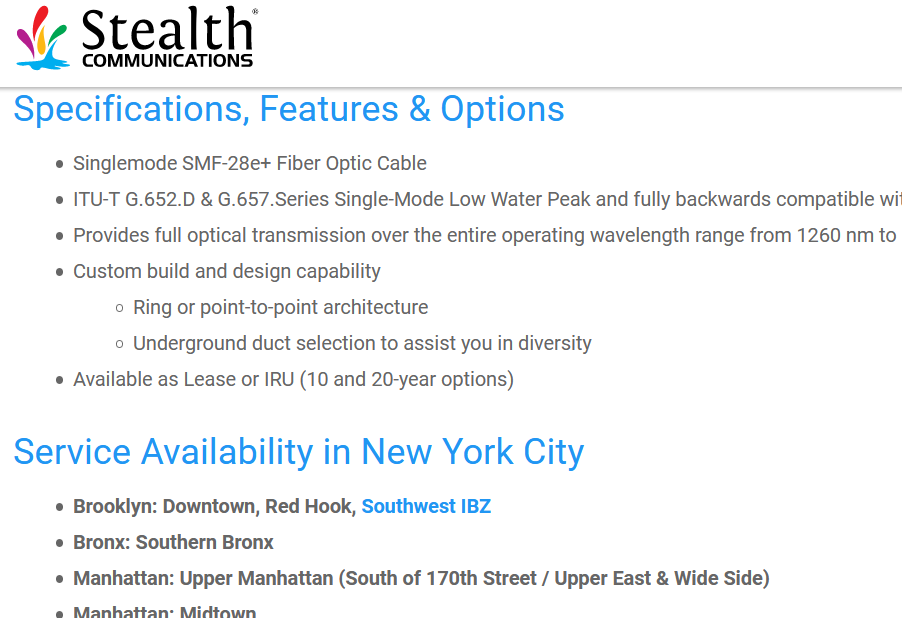
Dark Fiber Example 1

Dark Fiber Example 2
Alternative to Leased Lines: The Internet
From Tunnels and VPNs
Tunneling Protocols
- IP-in-IP: Simple and early approach directly supported by IPv4 and in the Linux kernel
- GRE (Generic Routing Encapsulation): Allows about any type of packet to be transported over IP, Linux support
- L2TPv3 (Layer 2 Tunneling Protocol): Provides optimized Ethernet over IP and tunnel control.
Securing Things
- Wikipedia: IPSec: “Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data to provide secure encrypted communication between two computers over an Internet Protocol network.” Works at the IP layer
- Wikipedia: OpenVPN: “OpenVPN is a virtual private network (VPN) system that implements techniques to create secure point-to-point or site-to-site connections…”, “It uses the OpenSSL encryption library extensively, as well as the TLS protocol, and contains many security and control features.”
Example VPN: WireGuard
WireGuard Basic Description
From WireGuard
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances.
WireGuard Cryptography
From WireGuard
WireGuard uses state-of-the-art cryptography, like the Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, HKDF, and secure trusted constructions. It makes conservative and reasonable choices and has been reviewed by cryptographers.
WireGuard Tunneling
From WireGuard
WireGuard securely encapsulates IP packets over UDP. You add a WireGuard interface, configure it with your private key and your peers’ public keys, and then you send packets across it. All issues of key distribution and pushed configurations are out of scope of WireGuard; these are issues much better left for other layers, lest we end up with the bloat of IKE or OpenVPN. In contrast, it more mimics the model of SSH and Mosh; both parties have each other’s public keys, and then they’re simply able to begin exchanging packets through the interface.
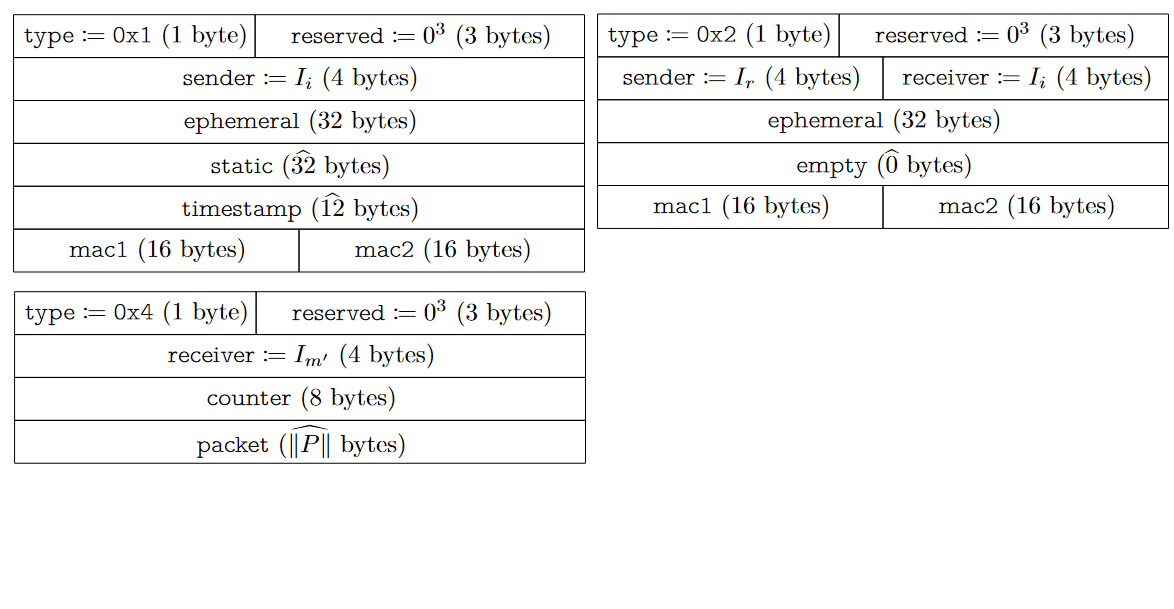
WireGuard Messages
From WireGuard WP
WireGuard Interfaces
From WireGuard
WireGuard works by adding a network interface (or multiple), like eth0 or wlan0, called wg0 (or wg1, wg2, wg3, etc). This network interface can then be configured normally using ifconfig(8) or ip-address(8), with routes for it added and removed using route(8) or ip-route(8), and so on with all the ordinary networking utilities. The specific WireGuard aspects of the interface are configured using the wg(8) tool. This interface acts as a tunnel interface.
Virtual Network Interfaces 1
From Wikipedia: TUN/TAP
In computer networking, TUN and TAP are kernel virtual network devices. Being network devices supported entirely in software, they differ from ordinary network devices which are backed by physical network adapters. TUN, namely network TUNnel, simulates a network layer device and operates in layer 3 carrying IP packets. TAP, namely network TAP, simulates a link layer device and operates in layer 2 carrying Ethernet frames. TUN is used with routing. TAP can be used to create a user space network bridge.
Virtual Network Interfaces 2
Uses and Platforms from Wikipedia: TUN/TAP
- VPN Examples: OpenVPN, OpenSSH, OpenConnect, WireGuard
- Virtual Machines Networking examples:Open vSwitch, QEMU/KVM, VirtualBox
- Platforms: FreeBSD, Linux, Windows, iOS/OS X, Android
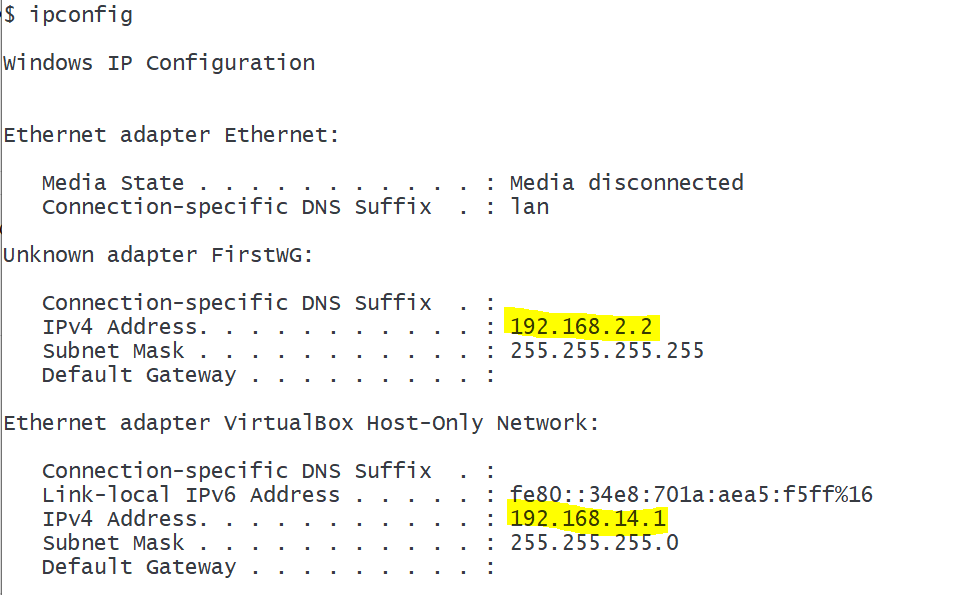
Example: Virtual Interfaces on Windows
WireGuard and VirtualBox interfaces on my laptop
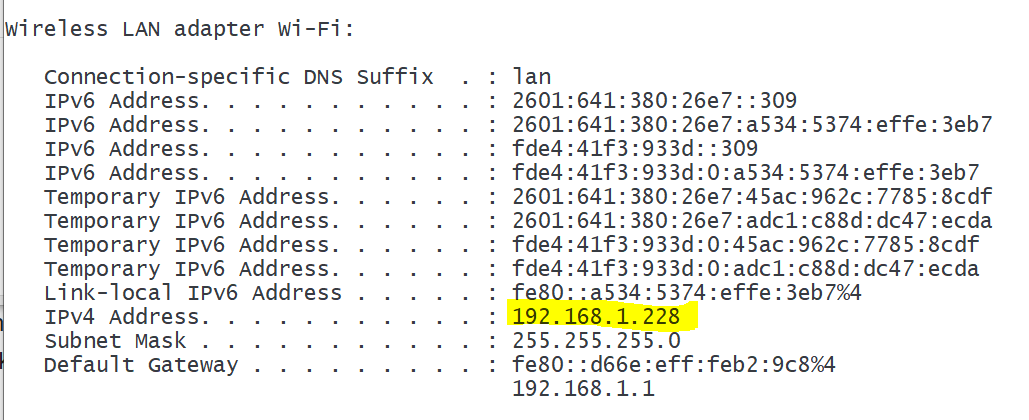
Example: Real Network Interface on Windows
Only my Wifi is currently connected here
WireGuard Demonstration Network
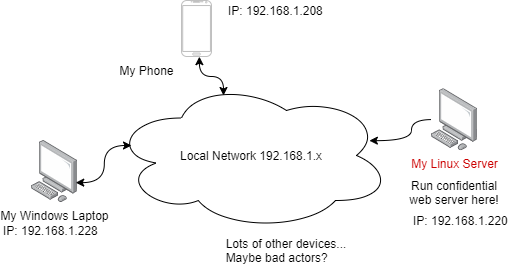
WireGuard Addresses
- Endpoint addresses: The real IP addresses for machines on local networks or the internet used by routers (switches)
- WireGuard Interface and AllowedIPs addresses: Addresses for the virtual WireGuard interfaces and MUST NOT correspond to networking addresses/prefixes already used by routers.
- My local network uses private 192.168.1.x addresses, so for this WireGuard demo I’m using private addresses in the range 192.168.2.x
Demonstration Addresses and Keys
- Laptop: endpoint address 192.168.1.228, WireGuard interface: 192.168.2.2, Public Key: RP80KtB6vOJh18qUt0plAOJQLqAdqMipu/FTNjDb0zs=
- Linux Server: endpoint address 192.168.1.220, WireGuard interface: 192.168.2.1, Public Key: Oq34hHw1jtr/88Q3iCeGOgbwdozZm9O8e+NW0uZrRmQ=
- Android Phone: endpoint address 192.168.1.208, WireGuard interface: 192.168.2.55, Public Key: VpJZ+OA9O+InevZTTFZrXkihZQqPtHg6uo1/JP24f2w=
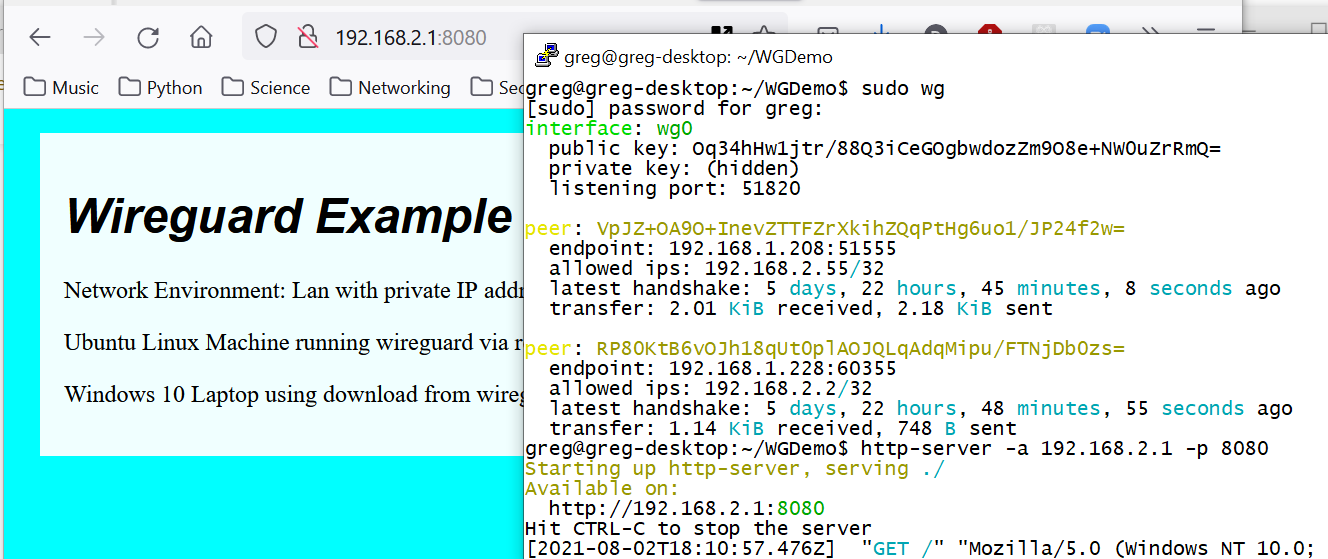
Confidential Web Page on Linux Server
- Set up a simple server http-server
- Bind the server to the WireGuard interface address 192.168.2.1
- Used TCP port 8080 for the server,
http-server -a 192.168.2.1 -p 8080
Client and Server Screens
Not really confidential info, but it could be
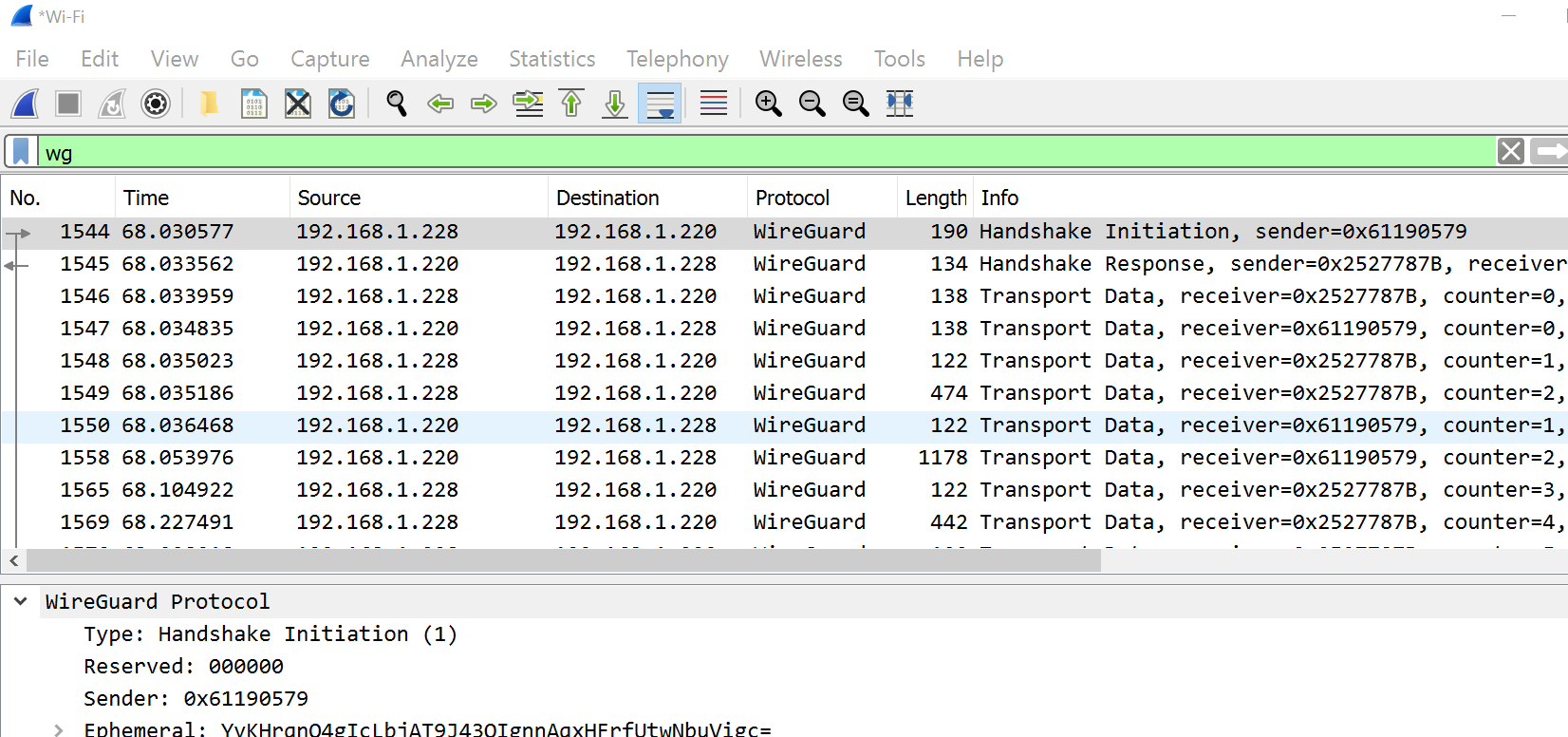
WireShark Traces 1
Can we tell WireGuard is being used by sniffing traffic
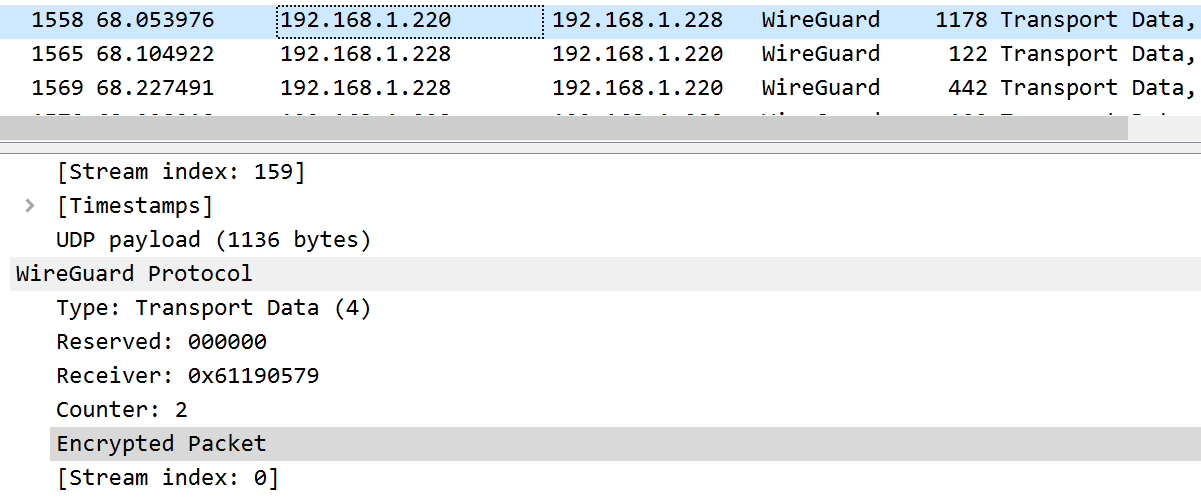
WireShark Traces 2
Can we tell that a client is talking to an HTTP server?
Anonymity
Beyond a Secure Connection
Who is “they” in each case below?
- “They” know your IP address and hence your location
- “They” know what site/service you are communicating with and where it is located
- “They” may be tracking you and identifying you via your browser
- “They” are constantly attacking (DDoS) your web site to prevent others from getting to it
VPNs for Anonymity
Idea: Use an “intermediary” (proxy) to forward your requests to the destination website so the web site will see the proxy’s address and not yours. See How to Choose a Good VPN. Let’s look at an open source example.
References: Tor
- Tor Home, Tor Metrics
- Tor Overview,
- Tor: Onion Services, Tor Design Paper
- Tor Slides sides 5-28 in particular.
Tor Overview 1
From Tor Overview
The Tor network is a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet. Tor’s users employ this network by connecting through a series of virtual tunnels rather than making a direct connection, thus allowing both organizations and individuals to share information over public networks without compromising their privacy.
Tor Overview 2
From Tor Overview
Individuals use Tor to keep websites from tracking them and their family members, or to connect to news sites, instant messaging services, or the like when these are blocked by their local Internet providers. Tor’s onion services let users publish web sites and other services without needing to reveal the location of the site.
Traffic Analysis
From Tor Overview
Using Tor protects you against a common form of Internet surveillance known as “traffic analysis.” Traffic analysis can be used to infer who is talking to whom over a public network. Knowing the source and destination of your Internet traffic allows others to track your behavior and interests. This can impact your checkbook if, for example, an e-commerce site uses price discrimination based on your country or institution of origin. It can even threaten your job and physical safety by revealing who and where you are.
Tor and Traffic Analysis
See Tor Slides 5-28.
Example: Home to Website
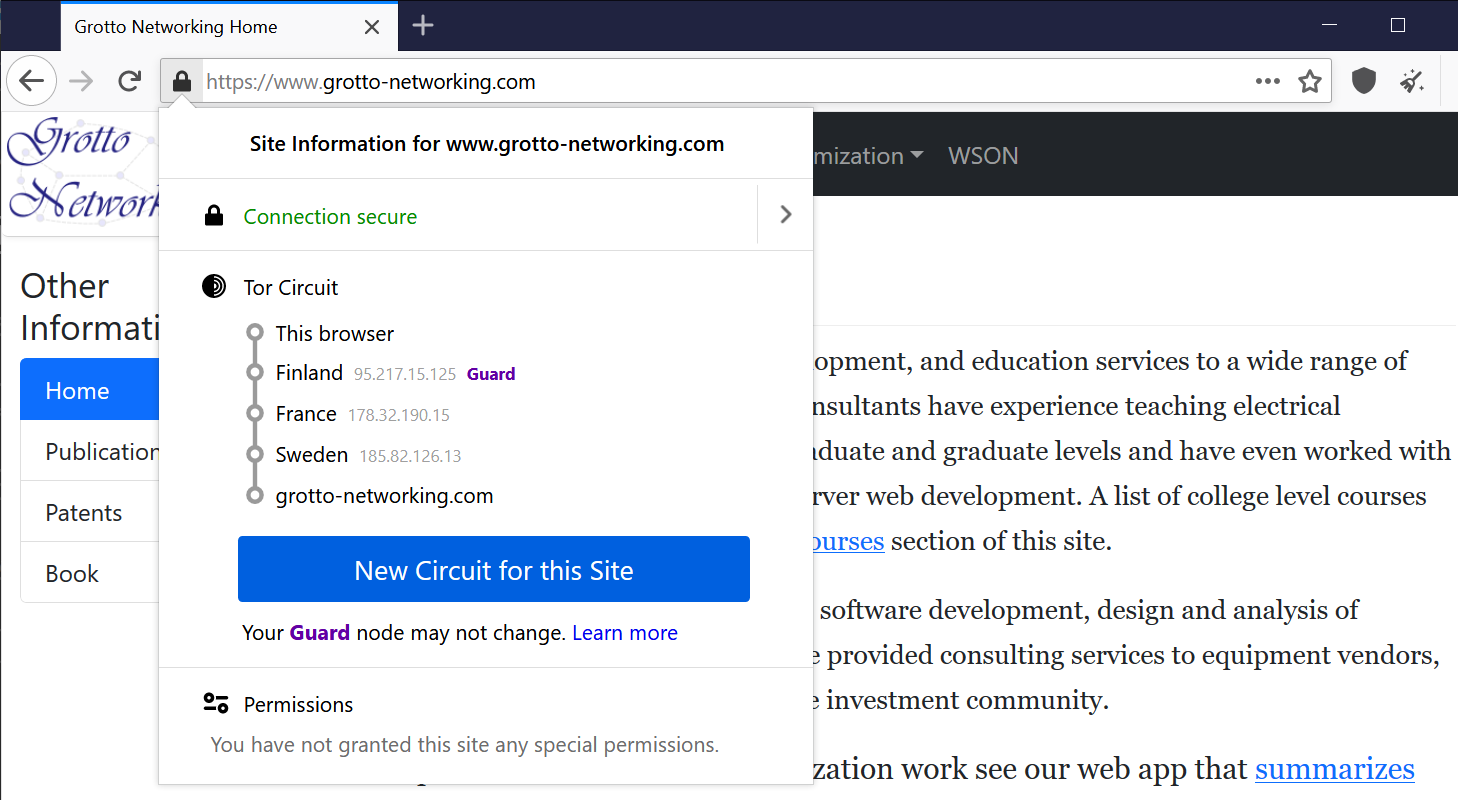
The Dark Web 1
From Wikipedia: Dark Web
The dark web is the World Wide Web content that exists on darknets: overlay networks that use the Internet but require specific software, configurations, or authorization to access. Through the dark web, private computer networks can communicate and conduct business anonymously without divulging identifying information, such as a user’s location
Dark Web Overlays
- Wikipedia: Tor (network)
- The Invisible Internet Project (I2P), I2P Intro has comparisons to Freenet and Tor.
- Freenet, Wikipedia: Freenet
Onion Services 1
From Tor: Onion Services
Tor makes it possible for users to hide their locations while offering various kinds of services, such as web publishing or an instant messaging server. Using Tor “rendezvous points,” other Tor users can connect to these onion services, formerly known as hidden services, each without knowing the other’s network identity.
Onion Services 2
From Tor Design Paper
Rendezvous points are a building block for location-hidden services in the Tor network. Location-hidden services allow Bob to offer a TCP service, such as a webserver, without revealing his IP address. This type of anonymity protects against distributed DoS attacks: attackers are forced to attack the onion routing network because they do not know Bob’s IP address.
Onion Service Overview 1
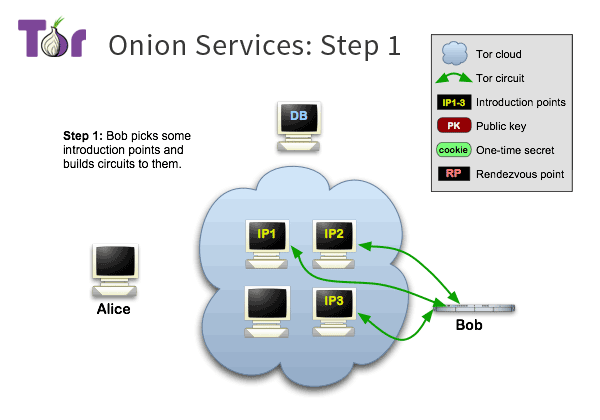
Onion Service Overview 2
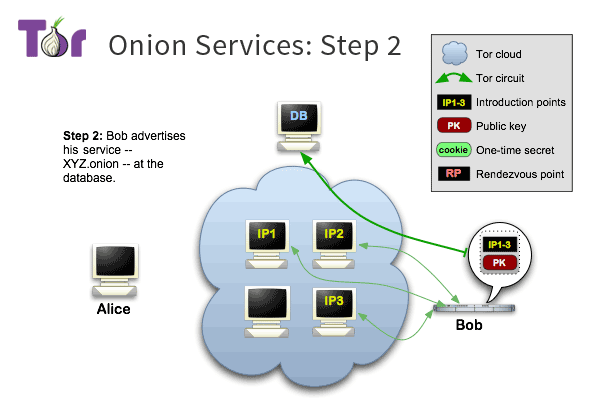
Onion Service Overview 3
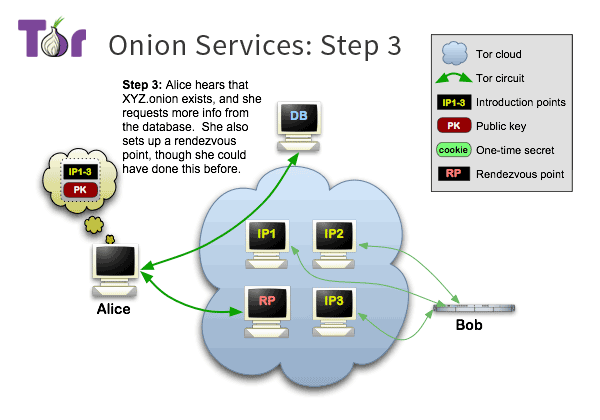
Onion Service Overview 4
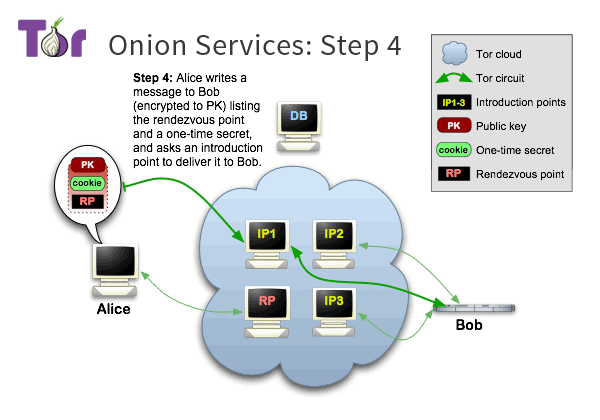
Onion Service Overview 5
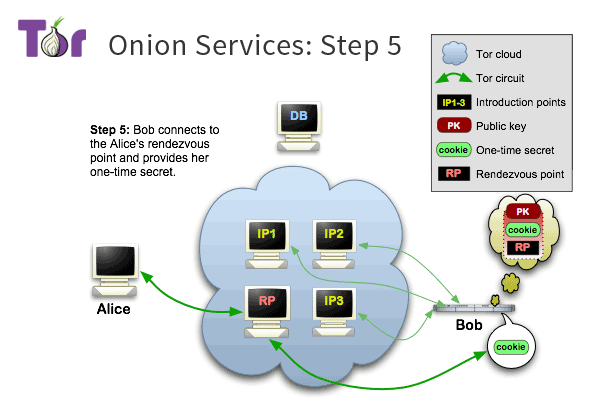
Onion Service Overview 6
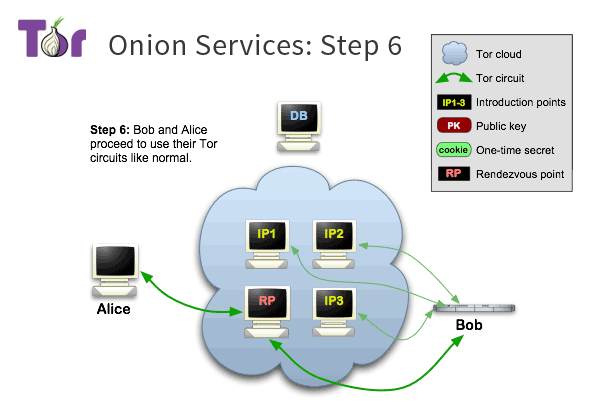
Onion Service Example
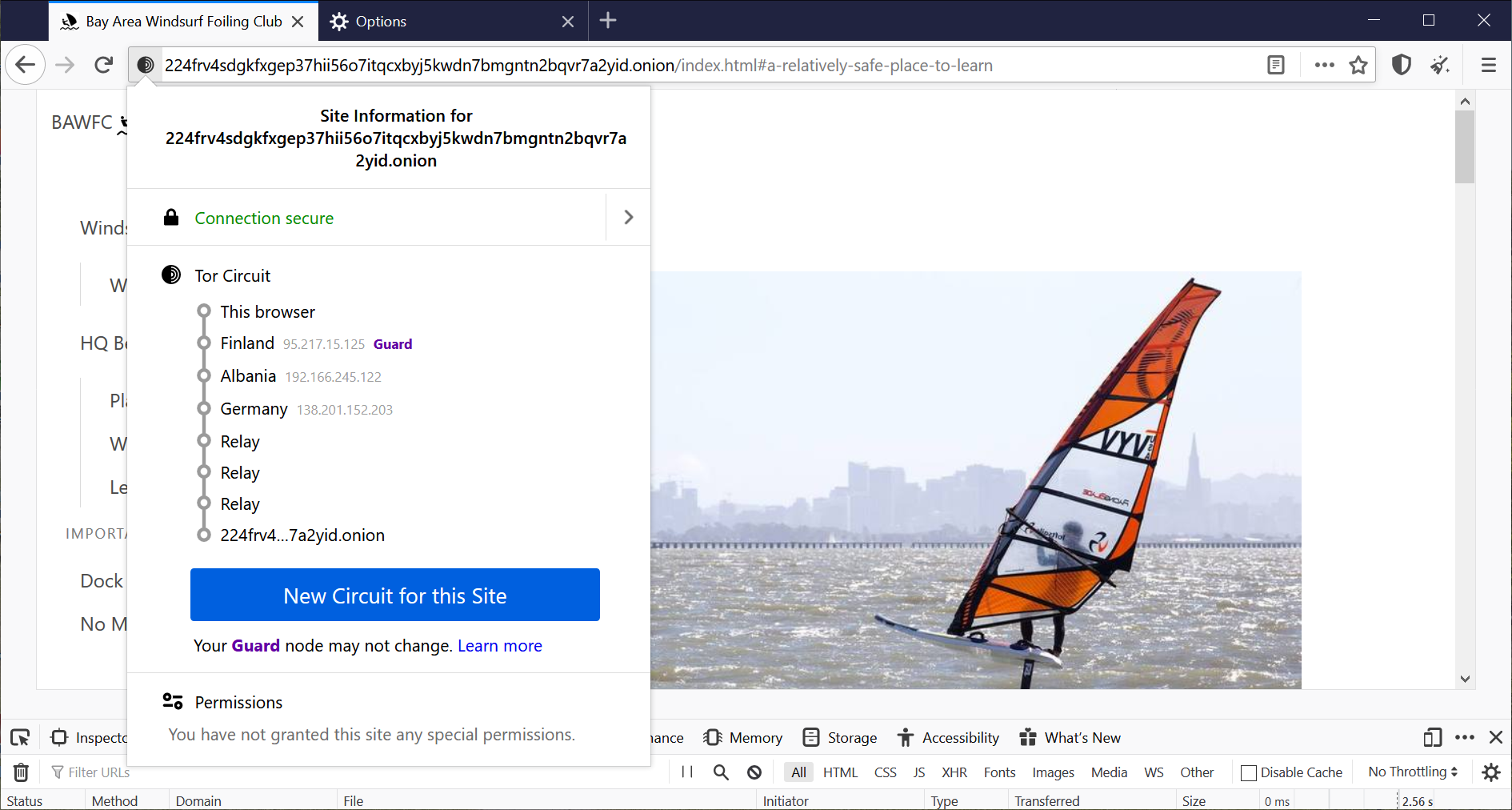
Useful Systems Using Tor
- OnionShare Easy secure sharing via Tor
- SecureDrop “SecureDrop is an open source whistleblower submission system that media organizations and NGOs can install to securely accept documents from anonymous sources”
- Tails “Tails is a portable operating system that protects against surveillance and censorship.”