Networking for Security
Dr. Greg Bernstein
January 29th, 2021
Networking for Security
Approach
Understand networking from the perspective of a Web Developer.
Generalize our knowledge of transport layer and above protocols. (This slide set)
Enhanced network understanding of the physical layer, network structure, management and control. (separate slide set).
CIA in Networking
- Who can see your information while in transit (being sent over the net)
- Who can modify your information while in transit?
- Who can prevent you from sending, receiving, information from a single site or the network in general?
Trace Route (Tracert)
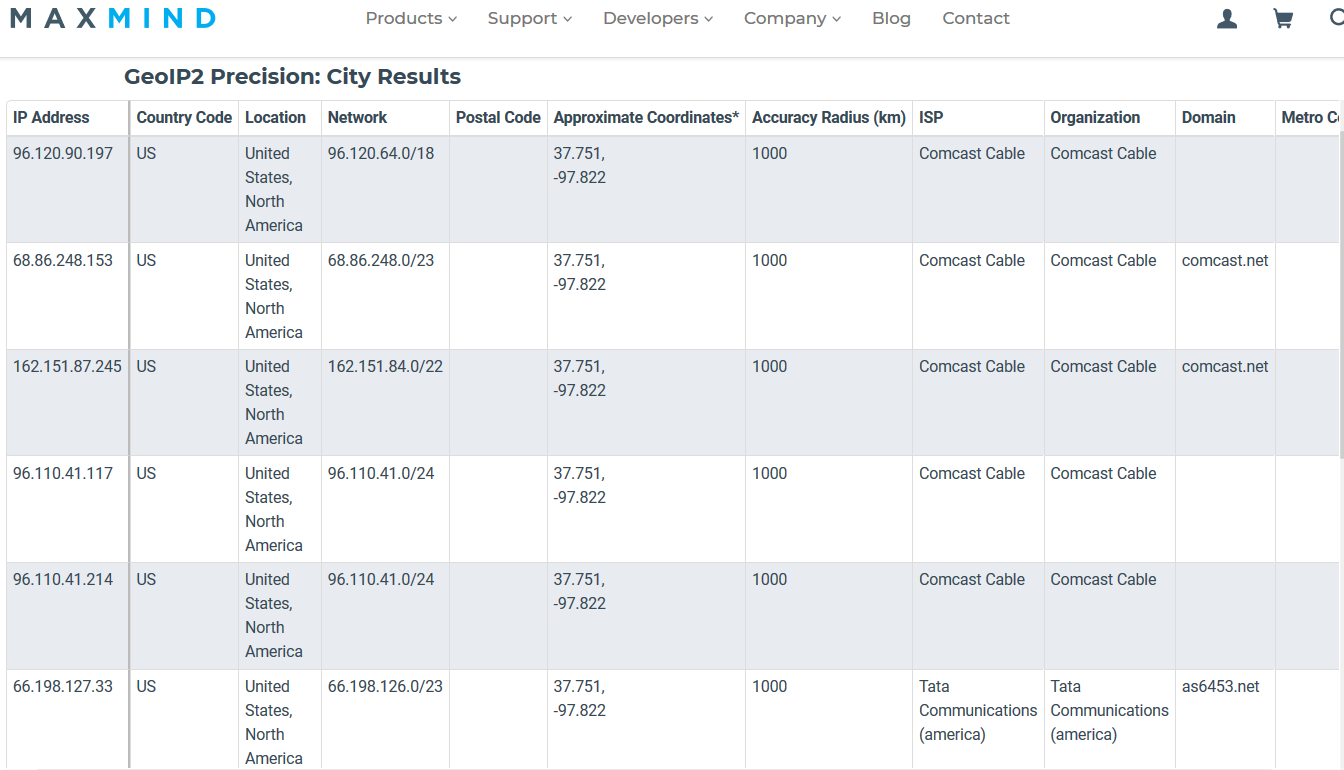
How many IP hops between my home to my web server?
$ tracert www.grotto-networking.com
Tracing route to www.grotto-networking.com [138.68.247.106]
over a maximum of 30 hops:
1 <1 ms 1 ms <1 ms OpenWrt.lan [192.168.1.1]
2 17 ms 10 ms 9 ms 96.120.90.197
3 8 ms 9 ms 8 ms 68.86.248.153
4 12 ms 13 ms 11 ms be-236-rar01.santaclara.ca.sfba.comcast.net [162.151.87.245]
5 13 ms 11 ms 13 ms be-39921-cs02.sunnyvale.ca.ibone.comcast.net [96.110.41.117]
6 19 ms 12 ms 11 ms be-3202-pe02.529bryant.ca.ibone.comcast.net [96.110.41.214]
7 30 ms 11 ms 11 ms ix-xe-0-1-1-0.tcore1.pdi-paloalto.as6453.net [66.198.127.33]
8 21 ms 17 ms 13 ms if-ae-2-2.tcore2.pdi-paloalto.as6453.net [66.198.127.2]
9 13 ms 12 ms 14 ms if-ae-5-2.tcore2.sqn-sanjose.as6453.net [64.86.21.1]
10 13 ms 12 ms 17 ms if-ae-22-2.tcore1.sf9-sanfrancisco.as6453.net [64.86.21.102]
11 * * * Request timed out.
12 * * * Request timed out.Locations 1
From MaxMind
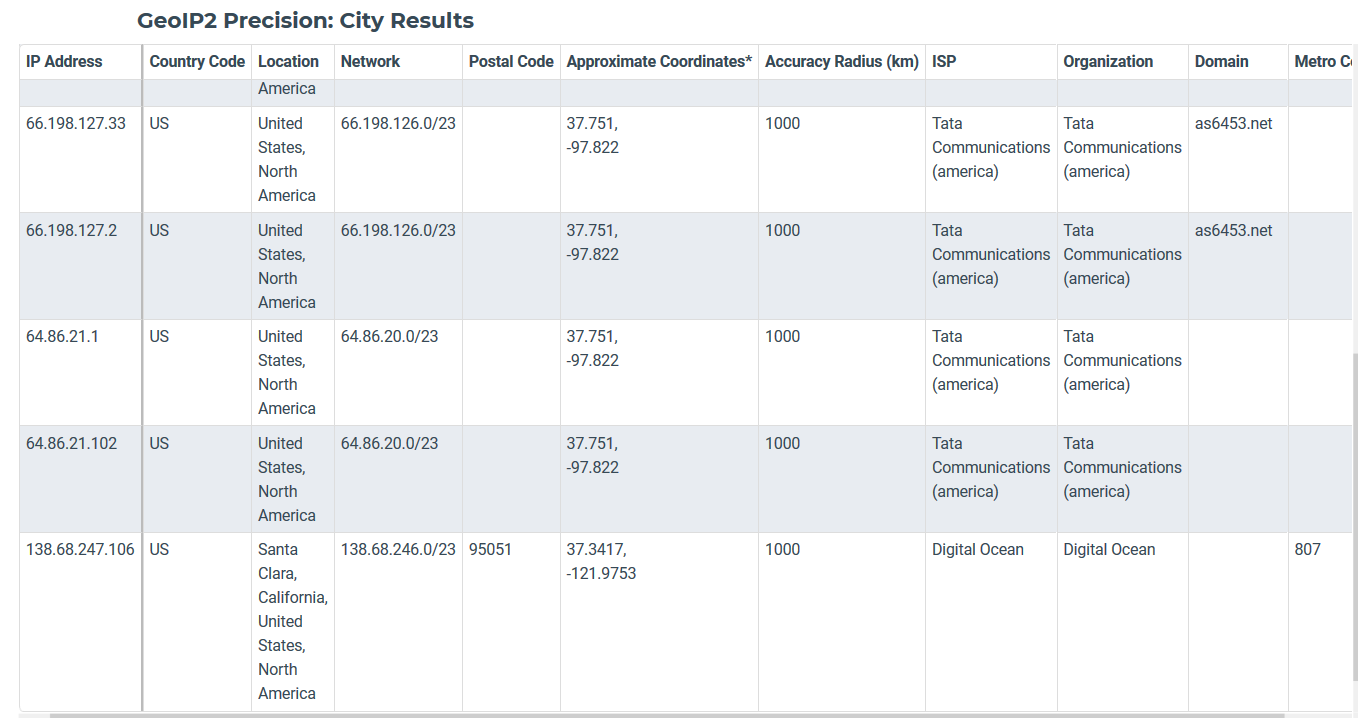
Locations 2
From MaxMind
On Ethernet but not IP
- IPv4, IPv6, ARP (Address resolution protocol – IP addresses to Ethernet addressses)
- VLAN-tagged frames (for traffic isolation in Ethernet networks)
- MPLS – Used for traffic engineering and high bandwidth VPNs
- Precision Time Protocol (PTP)
- And a bunch others some of which are no longer widely used…
“Transport Layer” Protocols (besides TCP, UDP)
- ICMP
- IGMP
- Tunneling: IP-in-IP, GRE, L2TP
- Routing: EGP, IGP, OSPF
- Signaling: RSVP
- Better transport: SCTP (Stream Control Transmission Protocol)
- and many others some new and some obsolete…
What and Why of Ports
Ports for Services
- For a computer to offer a network based service it must listen for requests (generic)
- Most services are built upon transport layer protocols
- The most common transport layer protocols are UDP and TCP
- Servers need to listen for requests on agreed upon UDP or TCP port numbers.
Ports (UDP and TCP)
Port numbers are assigned in various ways, based on three ranges: System Ports (0-1023), User Ports (1024-49151), and the Dynamic and/or Private Ports (49152-65535); System Ports are assigned by the “IETF Review” or “IESG Approval” procedures … User Ports are assigned by IANA using the “IETF Review” process… Dynamic Ports are not assigned.
Why Care for Security?
- Adversaries know which packets to snoop based on the port numbers! WireShark uses port numbers to help understand packet content.
- Port scanners check against these ports to see what services are offered by a machine
- Attacks are started with packets sent to particular ports!
Example 1: Tracking your Website visits
- HTTP uses TCP ports 80, 8080
- HTTPs uses TCP port 443
- We can snoop these packets obtain their destination IP addresses
- Use reverse DNS services to figure out the site visited (doesn’t always work)
Example 2: Tracking your Website visits
- DNS is not encrypted!
- Listen for TCP and UDP traffic on port 53
- Website domain name will be sitting there in plain text!
WireShark DNS Capture
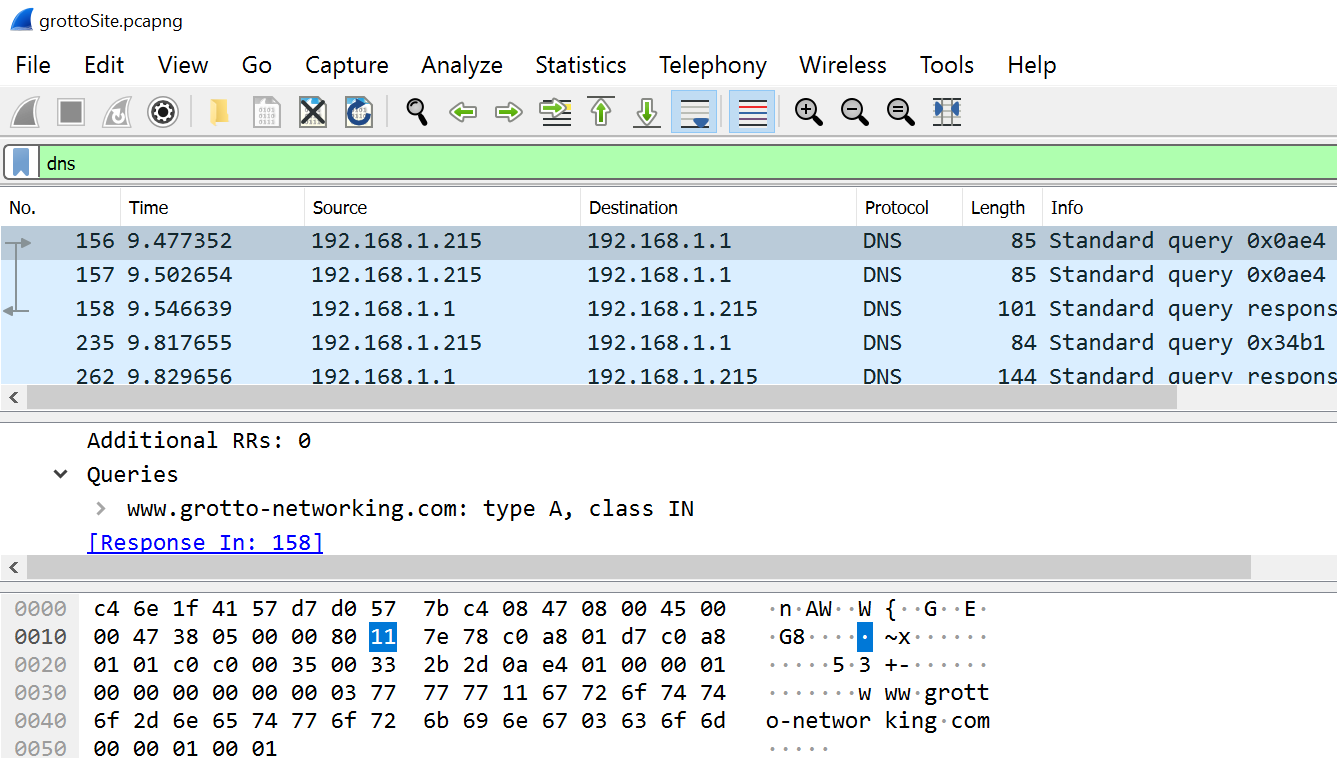
Kali DNS Tools
Is that how ISPs Spy on us?
- No, usually it is easier for them since they run the DNS server you usually use
- Even the simplest embedded DNS server software such as dnsmasq can produce logs:
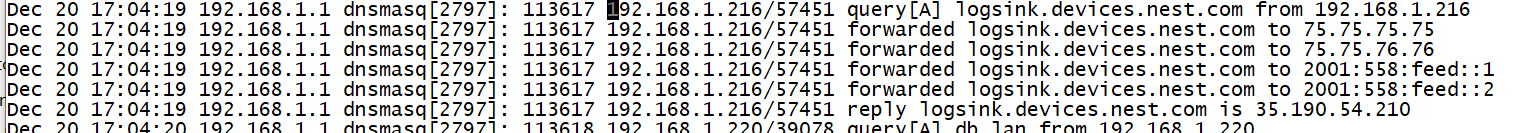
Most Hacked?
2014 list from Latest Hacking News
- TCP port 21 – FTP (File Transfer Protocol)
- TCP port 22 – SSH (Secure Shell) TCP port 23 – telnet
- TCP port 25 – SMTP (Simple Mail Transfer Protocol), TCP port 110 – POP3 (Post Office Protocol version 3)
- TCP and UDP port 53 – DNS (Domain Name System)
- TCP port 80, 8080, 443 – HTTP (Hypertext Transport Protocol) and HTTPS (HTTP over SSL)
- TCP and UDP port 135 – Windows RPC TCP and UDP ports 137–139 – Windows NetBIOS over TCP/IP, TCP port 1433 and UDP port 1434 – Microsoft SQL Server