General Instructions
The goals of this assignment are to get more familiar with DoS attacks, Botnets and start on email systems.
Create and Use a new Branch hw5
We will create a new git branch called hw5 for use in this assignment. The branch you create must exactly match the one I’ve given you for you to receive any credit for this homework.
Prior to creating this new branch make sure your working directory is “clean”, i.e., consistent with the last commit you did when you turned in homework 4. Follow the procedures in GitHub for Classroom Use to create the new branch, i.e., git checkout -b hw5. Review the section on submission for using push with a new branch.
Use README.md for Answers
You will modify the README.md file in your repo to contain the answers to this homework.
Questions
Question 1. (10 pts)
This problem you will need the free open source WireShark network protocol analyzer. You will learn about the reflected and amplified DoS attack that I demonstrated in class and described in the course slides. You will use the following packet capture files that I made for some of the questions: UnsolicDNSSmall.pcapng and UnsolicDNS.pcapng.
(a) WireShark and DNS Capture
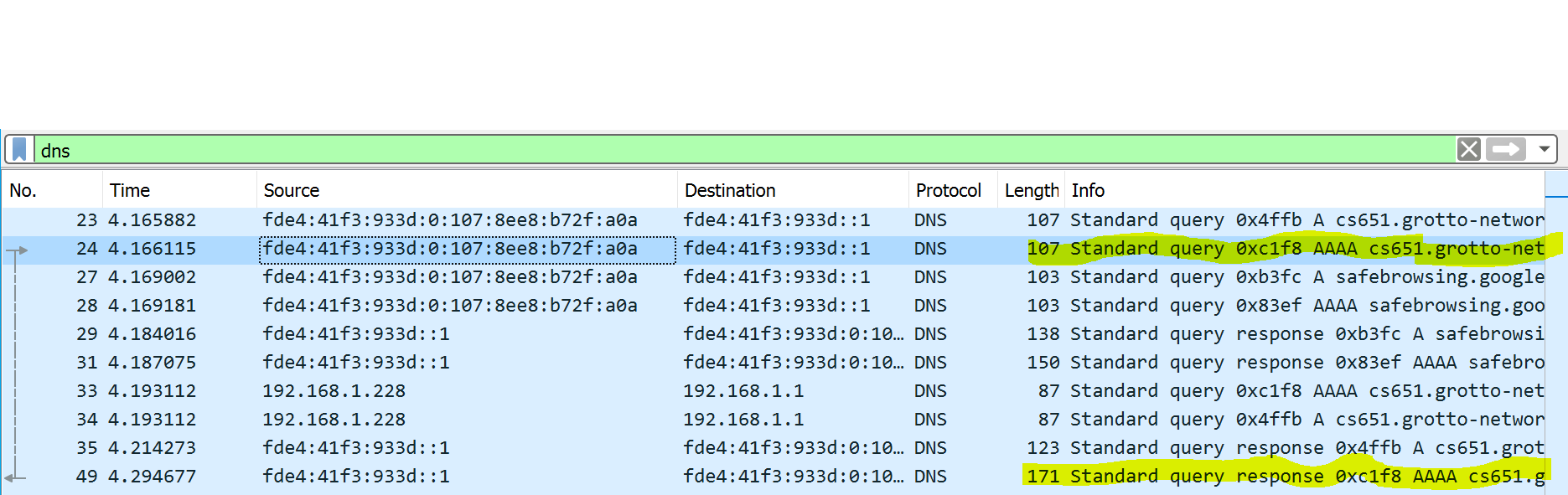
Capture a DNS request and response exchange with WireShark and show a screenshot here. Highlight the request and corresponding response in the screenshot. Notes: This is not as easy as it appears. First you need a way to trigger a DNS request. Second that request needs to be for “unsecured DNS”. For example if I try using FireFox which I have configured to use secure DNS (DNSSEC) I will not see any traffic recognizable DNS traffic with WireShark. Hence I triggered the DNS traces shown in my screenshot with Chrome. Finally when using WireShark you will tend to see a ton of packets, so you will generally need to put in a packet filter to restrict to just DNS packets.
Answer the following additional questions: (i) What is the domain name in your queries? (ii) What type of IP addresses are used by the machines for the DNS exchange? (iii) What type of DNS record was returned?
My screenshot looks like the following:
(b) Where to send the DNS response?
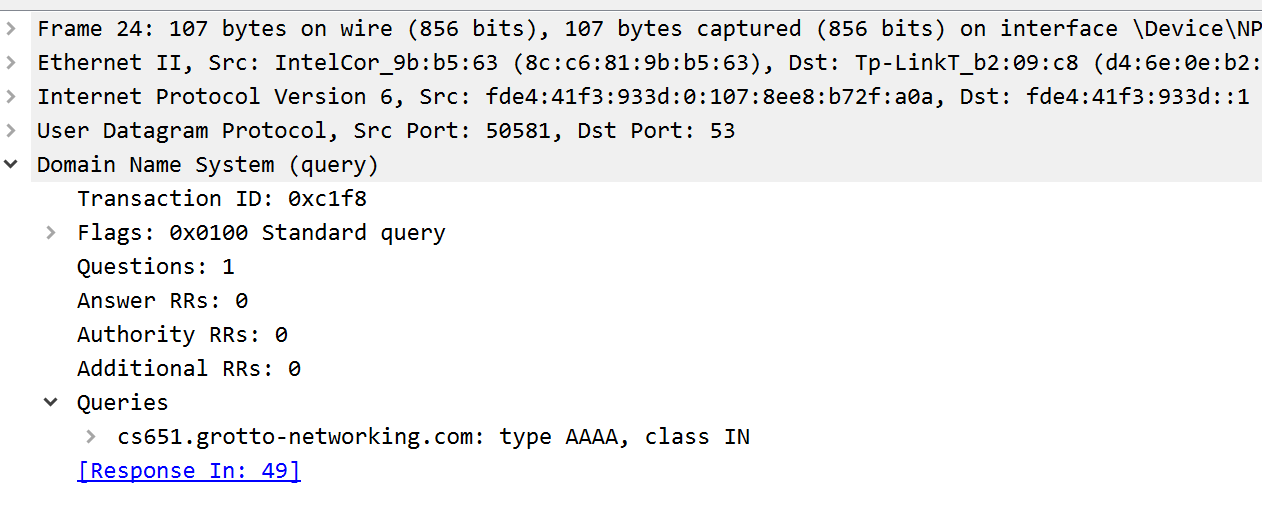
Look at the DNS request packet in WireShark. Where does the DNS server that receives this packet get the information for where to send the response. Write down that IP address here. Show me a screenshot of the packet details so I can verify.
My packet screenshot looks like:
Question 2. (10 pts)
(a) Why use reflection in an attack?
In my DoS attack on my laptop (IP address 192.168.1.228) the attacker was using my Linux machine (IP address 192.168.1.220). Open the packet capture file UnsolicDNSSmall.pcapng and look for DNS packets concerning the domain “www.grotto-networking.com”. Answer the following questions.
- Do you see both “queries and responses” or just “responses”?
- If my laptop didn’t ask for this information why was it sent?
- Who sent it?
- Can you tell from the packet who is responsible for it being sent?
- Why would an attacker use a reflection attack?
(b) Amplification in attacks
Using WireShark open the UnsolicDNS.pcapng and look for the “relatively” large unsolicited DNS messages received. Answer the following questions:
- How large is the Ethernet Frame? (in bytes)
- How large is the IP Packet?
- How many DNS resource records (total) are in the packet?
- What type of resource records (and their meaning) are in the packet?
- Why would an attacker want “Amplification”?
Question 3. (10 pts)
Botnet readings and podcast: EP 110: Spam Botnets, BOTNETS 101: INFAMOUS BOTNETS OF THE 21ST CENTURY, 9 of History’s Notable Botnet Attacks.
(a) The Cutwail Botnet
Answer the following questions concerning the Cutwail botnet (you may use the above or other sources from the Internet)
- What was the estimated number of computers used in the botnet when it was at its peak in size?
- What was the primary method of gaining access (infecting) machines to join the botnet?
- What was the botnet primarily used for? Or what was it most famous for?
(b) The Mirai Botnet
Answer the following questions concerning the Mirai botnet
- What was the estimated number of computers used in the botnet when it was at its peak in size?
- What was the primary method of gaining access (infecting) machines to join the botnet?
- What was the botnet primarily used for? Or what was it most famous for?
(c) Botnet uses
What are at least four illegal uses for botnets? List them here.
Question 4. (10 pts)
4(a)
What are the main components of a botnet?
4(b)
What information (two different types) can Bots be pre-loaded with so that they can access a command and control server when they are active?
4(c)
What types of protocols are typically used by bots to communicate with a C2 server? Which of these is least likely to raise suspicions and why?
Question 5. (10 pts)
5(a)
Which is older the Simple Mail Transfer Protocol (SMTP) or Hyper Text Transfer Protocol (HTTP)? Include when each was invented. Was security a major issue when SMTP was first created and used?
5(b)
What is MIME? How can MIME be used as an attack vector?
5(c)
In the context of email what are MUA and MTA? How do they work together and what protocol is used between them.
5(d)
What is an MTA? What protocol does an MTA used to talk with another MTA? Why are there more than one MTA?
5(e)
Why and where are the IMAP or POP3 protocols used?